
Protocol Corruption
ROLE
All Aspects
DESCRIPTION
In Protocol: Corruption, you play as antivirus software fighting to reclaim territory in a 1980s computer. This tactical tower defense game challenges you to strategically place Conquest Nodes to spread your color and build energy reserves while defending against waves of malicious viruses. Balance expansion with defense to conquer the infection and restore order. Will you succeed, or will the virus take control?
YEAR
2024
GENRE
Tower Defense
Engine
Unity Engine
PLATFORM
PC
Timeframe
10 weeks
Gameplay Overview
Orignal Systems
Scriptable Object Towers
-
Modularity for Flexible Gameplay:
-
Efficient Organization with Dictionaries
-
Minimal disruption to existing systems
-
Quick retrieval of key elements
-
-
Use of Scriptable Objects:
-
easy introduction of new units, nodes, or features.
-
-
Exposed Variables
-
Easy customization from within the inspector window
-



For this system, I designed a modular tower and conquest-node system using Scriptable Objects and dictionary-based lookups to decouple gameplay data from runtime behavior. This approach enabled rapid iteration, minimal disruption to existing systems, and the possibility of seamless introduction of new units, nodes, and features throughout development.
Technical Highlights
-
Data-driven tower and Conquest node definitions using Scriptable Objects
-
Dictionary-based organization for fast, reliable runtime lookup
-
Exposed inspector variables enabling non-programmatic tuning
-
Minimal coupling between data assets and gameplay logic
-
Scalable structure supporting new units and mechanics without refactoring
A* pathfinding
-
The Dynamic AI
-
random target selection for attacks.
-
Unpredictability forces players to reinforce defenses across multiple nodes.
-
Players must anticipate vulnerabilities and possible flanking opportunities from the AI.
-
Each surprise assault creates chaos, testing players' ability to maintain control.
-


For this system implemented a custom A* pathfinding system driven by spatial cost evaluation and distance-based heuristics, enabling AI agents to navigate environments efficiently while supporting dynamic target selection. World-space positions are converted into grid-space coordinates to allow consistent spatial reasoning independent of scene layout or object transforms.
Path selection is determined by accumulating movement cost between neighboring nodes and combining it with a heuristic distance estimate to the target, allowing agents to evaluate not just whether a route exists, but how efficiently it traverses space. This structure supports dynamic target selection without requiring changes to the underlying pathfinding logic.
As a result, AI units can dynamically reposition and flank, requiring players to reason about spatial coverage, approach angles, and node vulnerability rather than memorizing fixed paths.
Technical Highlights
-
World-space to grid-space conversion for consistent spatial reasoning
-
Custom A* implementation using distance-based heuristic cost evaluation
-
Separation of pathfinding logic from movement execution to avoid grid snapping
-
Direction-aware traversal between nodes supporting smooth, intentional motion
-
Dynamic target selection layered on top of spatial path cost evaluation
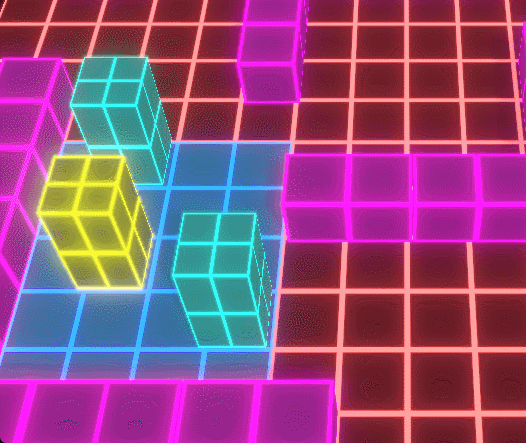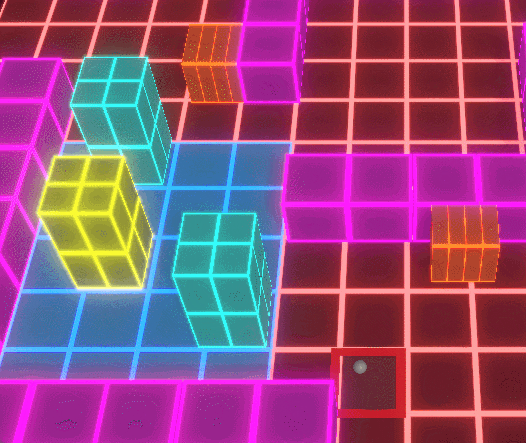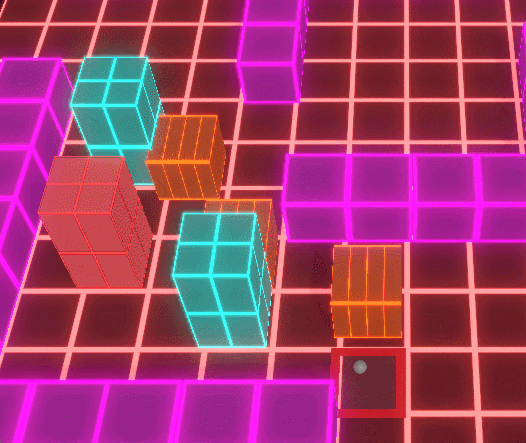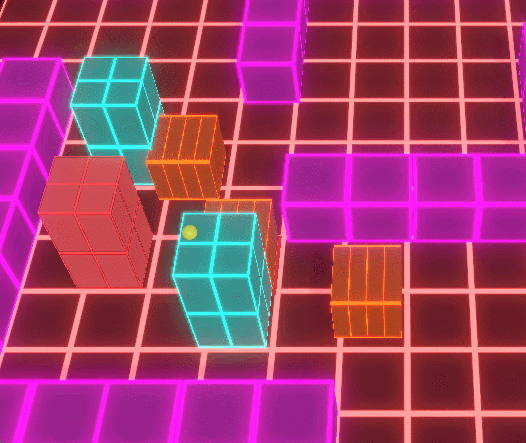
Conquest Nodes
-
The Conquest Node System allows players to capture and control territory,
-
Players deploy Conquest Nodes to strategically expand their influence across the map,
-
-
players must manage their defenses to protect against enemy AI incursions.
-
Enemy AI poses a significant threat, as it can corrupt player units, turning them against their former allies.
-
Corrupted units disrupt player strategy, adding layers of intensity and risk to encounters.
-
-
Mastering Conquest Nodes is essential for dominating the corrupted environment and pushing back hostile forces.
-
This creates a loop of strategic capture, defense, and effective resource management.
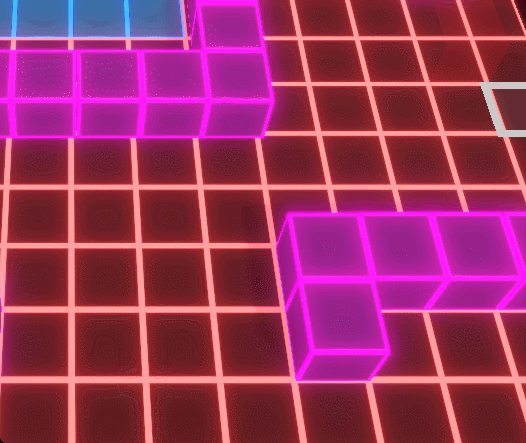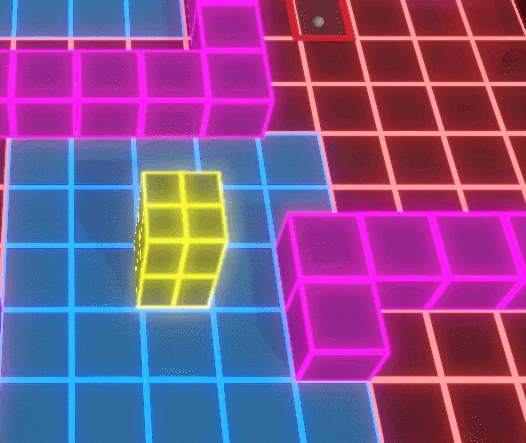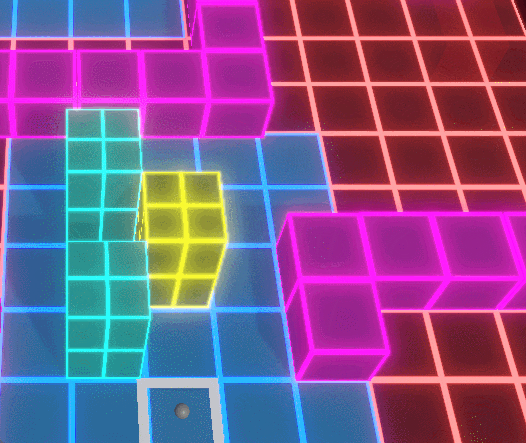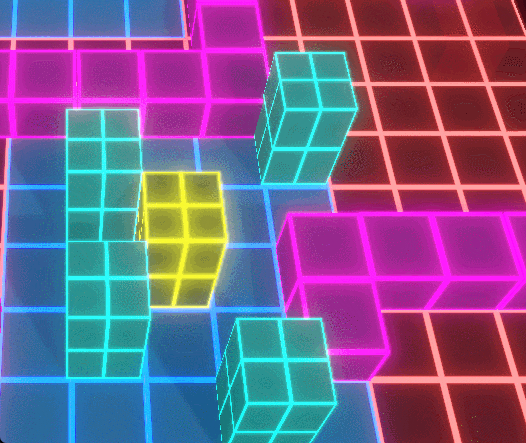


The Conquest Node system forms the strategic backbone of Protocol Corruption, allowing players to capture, defend, and expand territory across a modular grid-based map. Nodes act as spatial anchors that define player influence, resource flow, and defensive placement, turning the environment itself into a contested gameplay system.
When a Conquest Node is captured, ownership state propagates outward through associated systems, updating influence areas, available placement zones, and connected defensive structures. This ensures that territory control is not cosmetic, but directly affects where players can build, reinforce, and respond to enemy pressure.
Path selection is determined by accumulating movement cost between neighboring nodes and combining it with a heuristic distance estimate to the target, allowing agents to evaluate not just whether a route exists, but how efficiently it traverses space. This structure supports dynamic target selection without requiring changes to the underlying pathfinding logic.
As a result, AI units can dynamically reposition and flank, requiring players to reason about spatial coverage, approach angles, and node vulnerability rather than memorizing fixed paths.
Enemy AI introduces counterplay by corrupting captured nodes and nearby units, dynamically reversing ownership and converting previously safe areas into hostile zones. Because corruption operates on the same spatial rules as player control, territory remains fluid, forcing players to continuously reassess positioning, coverage, and defensive priorities.
By tightly coupling node ownership, influence validation, and AI interaction, the system creates a gameplay loop centered on spatial control, risk management, and adaptive defense, rather than static base building.
Technical Highlights
-
Grid-based territory nodes acting as spatial control anchors
-
Ownership state propagation affecting influence areas and build validation
-
Dynamic conversion of player-controlled nodes by enemy AI
-
Validation of placement and interaction based on spatial influence checks
-
System-wide state updates triggered by node capture and corruption
Onboarding Players
.png)
%20(1).jpg)








